When and How to Use 20mhz vs 40mhz vs 80mhz
The term "network" is one of the core terms of IT which the industry relies on the most. In plain terms, a network is a group of devices that can communicate with each other using a link. We call these devices as hosts, and all the hosts have their unique identity addresses. Read more to learn about the major concepts of networking and Wi-Fi that everyone should know.
10 Front-End Web Developer Portfolios to Inspire You
Web developers are in high demand now. However, as the demand grows, so does the supply. The number of people in this profession is growing
How to Build a Standout Portfolio for Software Engineering Job Applications
Prioritize project details, outcomes, documentation, and readability when building a software engineering portfolio to showcase your development skills.
How Do I Protect a Computer Network? 4 Cybersecurity Tips
Consistently protecting a computer network means implementing strong password policies, keeping software systems up to date, using network security tools, and pursuing continual education in cybersecurity best practices.
ITIL 4 Foundations Certification: Why It's Valuable For IT Professionals
An ITIL 4 certification provides globally recognized expertise in IT service management, enhancing your career prospects, increasing your earning potential, and improving your organization’s internal efficiency.
Information Technology vs. Computer Science: What's the Difference?
Information technology (IT) focuses on the practical application and management of technology infrastructure, while computer science (CS) embraces theoretical study and the development of algorithms, software, and computing technologies.
Is an IT Bootcamp Worth it? Benefits of IT Bootcamp Training for Career Switchers
IT bootcamps are made for aspiring professionals looking to develop skills in cybersecurity, software development, cloud computing, data visualization, and other information technology basics.
Tech Layoffs? The Hidden Job Boom in the Tech Industry
Despite trending layoffs from top-tier tech companies, hiring overall in the tech field is still consistent, particularly for top-earning cybersecurity, networking, and software positions.
Demystifying Tech Layoffs: Distinguishing Fact from Fiction
Tech layoffs typically indicate economic turns, internal restructuring, industry consolidation, or shifts toward new technologies that ultimately create new opportunities for tech professionals to upskill and thrive.
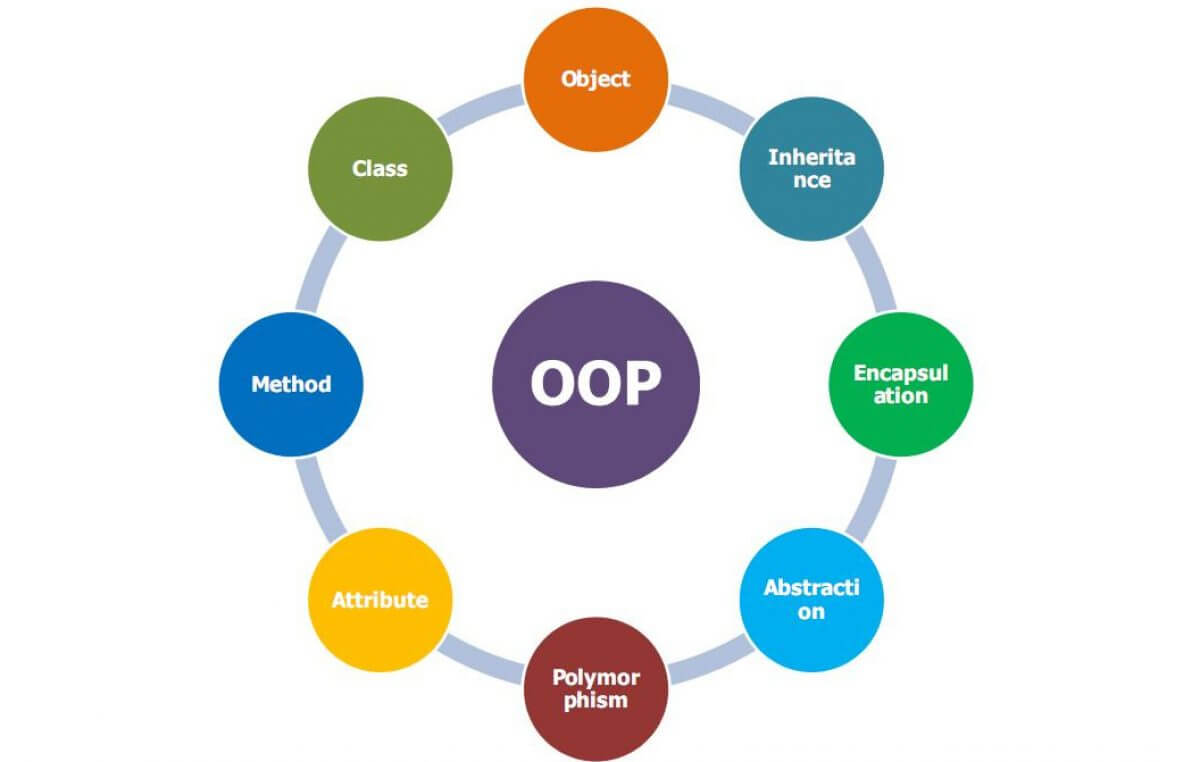
Abstract Classes vs. Interfaces: Decoding the OOP Dilemma in Software Engineering
Abstract classes provide a blueprint for classes, allowing a mix of abstract and concrete methods, while interfaces define contracts for classes, supporting multiple inheritance and enforcing method implementation.
10 Applications of Object Oriented Programming
Getting started with object oriented programming? Here are 10 applications of object oriented programming (OOP) that you should know about.
Mastering Object-Oriented Programming in Python: Applications and Key Concepts
Object-Oriented Programming (OOP) in Python is a programming paradigm that organizes code into objects, each of which encapsulates data and behaviors, promoting modularity, reusability, and a clear way to model and interact with real-world entities.