The CompTIA Training Series: Identifying TCP/IP Network Implementation
The Internet is practically an endless void of knowledge, consisting of countless sources and data points, across the globe. So, how exactly did the internet become such a huge repository of information, especially when it is not owned by any entity?
The internet, and the World Wide Web, connects many networks together. These interconnected networks host information on the World Wide Web for others to access, though it does not happen without a few set procedures.
Taking an example of us human beings; when we communicate with each other, what is the biggest factor that determines understandability between two people? “Language.” It is also the most significant communication barrier. For one person to understand speech from another, they need to have at least a rudimentary understanding of the language. Similarly, when computers talk to each other, the other computer must be able to comprehend data from the host.
Thus, protocols were established. Protocols are set guidelines and rules used to interconnect networks on the Internet in order to exchange information.
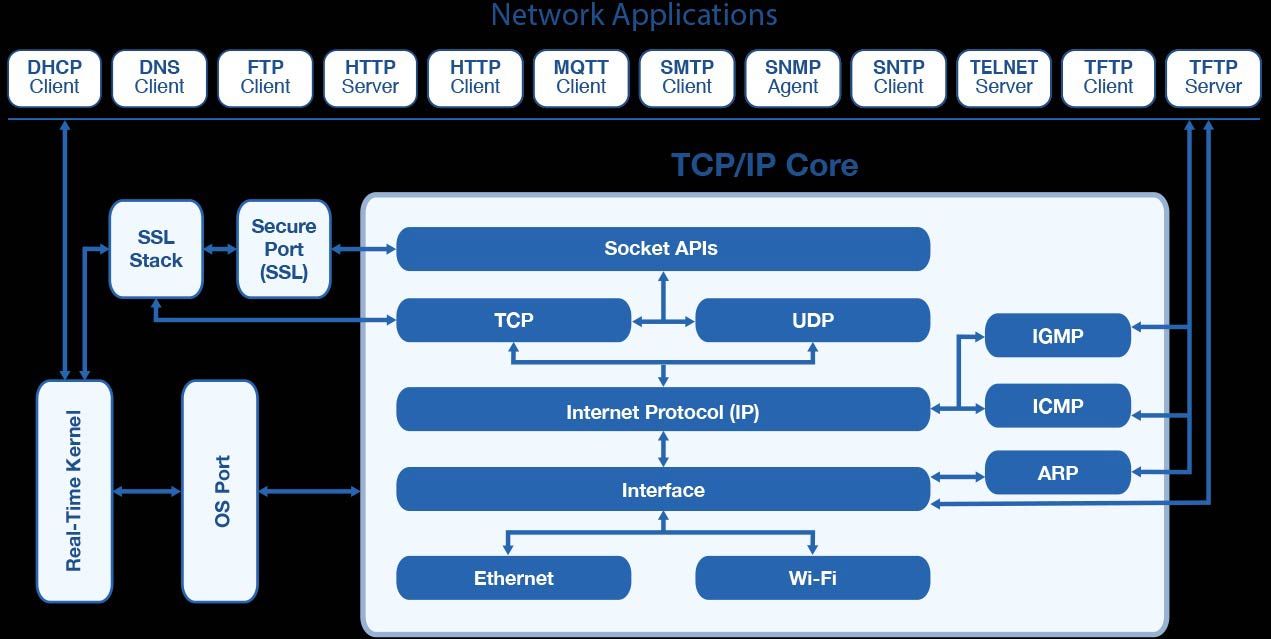
TCP/IP is the suite of two protocols that bridge networks on the Internet. It dictates how information is to be sent and received, and determines the correct destination. It is also known as the DARPA model, which refers to the U.S government agency that initially deployed it.
As mentioned earlier, TCP/IP is a combination of two separate protocols: Transmission Control Protocol (TCP) and Internet Protocol (IP). The former dictates how data will be transmitted as small packets of information and reassembled in the right order when it arrives at the destination. The latter directs the data where to go and how to get there.
TCP also ensures the integrity of data. It runs checks on packets for errors to determine whether the entire package was sent correctly, and retransmit them if necessary. A simple example can be derived from how teleportation is theorized. Everything in the universe is made up of atoms, even living beings. To teleport an object from one place to another, we would have to break down the molecular structure of that object and reconstruct it at the destination point.
In order for “Hello” to be transmitted, TCP would break the word into small packets and ensure that when the packets arrive at the intended destination, the letters rearrange in the correct manner to spell “Hello”.
The functionality of TCP is organized into four abstraction layers, each with its own related protocols.
- Application Layer
- Transport Layer
- Network Layer
- Link Layer
Application Layer
This layer describes communication with applications through some set standards. There are various protocols involved, including HyperText Transfer Protocol (HTTP), File Transfer Protocol (FTP, Simple Mail Transfer Protocol (SMTP), Domain Name System (DNS), Post Office Protocol 3 (POP3), and Simple Network Management Protocol (SNMP).
Anyone who has used a web browser to open a website on the internet must remember seeing “HTTP” in the address. It is the protocol used when we request our browser to access a web server. Similarly, when we download or upload a file from the web server, we initiate an interactive user session by requesting the FTP protocol. SMTP is used to transfer mail and attachments.
Transport Layer
The transport layer deals with the end-to-end communication between the host and the destination. It handles the functionality of converting data into packets and sending it to its destination. Like an application layer, the transport layer uses two protocols: Transport Control Protocol (TCP) and (User Datagram Protocol) UDP.
The two vary in terms of reliability. UDP does not bear the responsibility of error checking when data is sent. It is used when the data to be transferred is small enough to fit in a single packet. TCP, on the other hand delivers reliable transmission of data by performing error detection and determining whether packets need to be retransmitted.
When data is received by fellow TCP/IP protocol at the destination, it checks the sequencing order of the packets stamped before transmission, and sorts them in order. The host receives acknowledgement from the destination, and the packet is subsequently retransmitted.
Network Layer
The Network Layer initiates connection with other networks for the delivery of data packets. Similar to Application Layer, this layer has its own protocols. These include Internet Protocol (IP), Internet Control Message Protocol (ICMP), Address Resolution Protocol (ARP), Internet Group Management Protocol (IGMP), and Internet Protocol Security (IPsec).
Data packets are sent out containing the IP header. The router checks the IP address of the target destination. The process continues, from one router to another, until the destination address is a match.
Link Layer
The link layer is divided into two sublayers: Physical Layer, Logical Link Control (LLC), and Media Access Control (MAC).
The physical layer manages how data is physically sent through the network. Bits can change form depending on the network medium, such as coaxial cable, optical fiber, or twister pair copper wire. Wired mediums dictate whether the link layer converts data frames into electrical signals or in the form of electromagnetic waves when wireless communication is involved. These signals are converted back into data frames and assembled, following the respective function of each of the aforementioned layers.
The link layer also works to determine collisions when nodes try to transmit frames at the same time, and how devices can recover from them.
LLC functions to control data flow among various applications. It puts up corresponding protocols during delivery of the data packet. MAC acts as an interface between LLC and the physical layer. It adds source and destination addresses to the data frames.
It also allows identification of devices in the network. MAC addresses differ between Ethernet and 802.11 wireless specifications. Your laptop’s MAC address, when connected with an Ethernet cable, will differ from the MAC address when using a wireless connection.
That article some of the basic information on TCP/IP protocol and its functions. CompTIA training is a great way to instill advanced networking knowledge if you are looking to learn more. Not only that, but CompTIA training programs will also enable you to appear for CompTIA’s professional certification.
